This Easter we launched our 2nd cyber puzzle challenge with a handful of prizes to be won for those Forensic Foxes that helped us track down our escaped Rabbit.
We were delighted to have players from across 28 countries join in but it looks like this was a tough one though, as only one person successfully completed our challenge and caught the Rabbit 🐰. The only person to claim the top prize of a free
Browser History Examiner (BHE) Pro licence worth $525 USD and Amazon voucher was @Tristan04375166. An honourable mention also goes to Cameron Stiller for being the only player to solve the difficult
Easy as Pi challenge!
Congratulations to Tristan and Cameron, but for all those who joined in this time we’ve written a detailed walkthrough below.
On the challenge page (https://challenges.foxtonforensics.com) players were informed the Easter bunny had lost track of time while self isolating and were asked to help find him and remind him he needs to turn up to work in time for Easter as the government confirmed he was a key worker! Players needed to discover each of the challenge flags to help locate Rabbit 🐰 and get him back to work. The first challenge is called Tricky Media.
Tricky Media
We’ll have to capture lots of flags to reveal the clues we need to track down Rabbit.
We’ve been reliably informed the first flag is buried in this Google Chrome history file. The last time someone saw Rabbit was 24th March 2020, does that help at all?
Players are invited to start the first challenge by downloading a Google Chrome history file called
Favicons. This is a SQLite database file which the players can view using a SQLite viewer such as our free tool
SQLite Examiner.
This favicon blob image data can be exported out for further analysis in a hex viewer as shown below.
At the end of the image binary there is an additional string
=EyPHd0MZ10UFJVRIdFVJJkQ0I1RBxkR
This can be decoding using
CyberChef. Extracted out and reversed gives
RkxBR1I0QkJJVFdIRVJFU01ZM0dHPyE=
Decoded from Base64 gives
FLAGR4BBITWHERESMY3GG?!
This is the first flag the player can enter into the challenge CTFd website.
FLAG
FLAGR4BBITWHERESMY3GG?!
The HINTS for this challenge were:
Wait a minute... not all these favicons are alike…
Grab dat blob!
Pandemonium
Nobody has seen Rabbit for weeks now but he did leave behind some clues...
Players are provided with a JPG file to download named qTiHcX0.jpg.
Analysing this JPG image in a hex editor reveals what look like “PK” ZIP signatures at the end of the file content. This hidden data can unpacked on the command line using the following:
unzip qTiHcX0.jpg
Unpacking the extracted ZIP archive reveals the 4 files shown below.
3 are PNG images of equations, 1 is a JPG meme which is shown below.
The first flag is printed near the top of the JPG image.
This is the flag the player can enter into the challenge CTFd website.
FLAG
FLAGWASHYOURRABBITPAWS!
The HINT for this challenge was:
Is this really a normal image file? Maybe if we treat it as if it were some other type of file...
Easy As Pi
Equations? These clues are getting more complicated!
Do we have any mathematicians that can help with the next flag?
The 3 PNG Images extracted in the previous challenge show equations that when solved result in some useful numbers.
These equations can be solved using the
Wolfram website. The players can use this website to work out what x equals for each equation.
PNG Equation 1
Solving the equation (x-log(9))/5 = log(4)^2/sqrt(6) results in the approximate result
x = 6.12010700894255
Ignoring digits after 00 null operator leaves us with 6.120107
06120107
Changing these digits to text using A=1 B=2… etc.
The decoded text is FLAG
PNG Equation 2
Solving the equation log_2((log_7(x))+1) = -(sqrt(2)^pi/7) results in the approximate result
x = 0.609021514000363
Ignoring digits after 00 null operator leaves us with 0.609021514
0609021514
Changing these digits to text using A=1 B=2… etc. gives FIBON
PNG Equation 3
Solving the equation x/((log_9(x))+1) = pi-2 sqrt(3 pi) results in the approximate result
x = 0.103030900000002458083808097
Ignoring digits after 00 null operator leaves us with 0.1030309
01030309
Changing these digits to text using A=1 B=2… etc. gives ACCI
Adding the 3 strings together makes FLAGFIBONACCI
FLAG
FLAGFIBONACCI
The HINTS for this challenge were:
Maybe a wolf can help you resolve the numbers? At least those up to NULL…
Rabbit must have spent ages putting these equations together!
Golden Ticket
We need to move quickly to find Rabbit in time for Easter and we’d normally check Pastebin for clues... but we don’t have time for that right now. Less paste more haste!
Use your flag from the Pi challenge to help in your search!
Players are provided with a PNG file to download named 4.png.
Searching for the previous flag on Google, the player can quickly find the familiar golden spiral shape.
Applying this fibonacci sequence to the letters in the 4.png image forms the following string.
QUICKACCESSURLAVIPUQIPAQ
QUICK ACCESS URL AVIPUQIPAQ
Rather than PASTEbin they can find the next flag on HASTEbin using the above code to build the full URL.
This webpage had a new flag on it.
FLAGSL0WLYSL0WLYCATCHYRABB1T
The player can enter this flag into the challenge CTFd website to continue.
FLAG
FLAGSL0WLYSL0WLYCATCHYRABB1T
The HINT for this challenge was:
Hmm this sounds pretty similar to something I had to solve to catch Rabbit in the last Cyber Challenge!
Bump in the Code
If you’ve tried to catch him before you’ll know sometimes the Rabbit can be seen on Twitter dropping clues to all the foxes chasing him. Ignore his chatter then go to the main challenge page to continue!
https://challenges.foxtonforensics.com
If players read the walkthrough for the first Foxton Forensics cyber challenge they will see a Twitter account was used for the Rabbit named
@foxtonrabbit. Visiting this account reveals only one tweet shown below.
This is braille and can be decoded on CyberChef to read
CKHOANTATMEIR
The initial clue suggested players Ignore the rabbits chatter so remove the CHATTER letters from the string leaving the word KONAMI.
A simple Google search for Konami shows lots of examples of a cheat code
UP UP DOWN DOWN LEFT RIGHT LEFT RIGHT B A
Again following the clue players are told to go to the main challenge page where they can enter the cheat code, which reveals a pop up box!
This is the next flag.
FLAG
3LM3RFUDD
The HINT for this challenge was:
I'm definitely getting more time to play video games during this time in isolation!"
Ace in the Mole
The next url gave me flag dejavu but it’s all you need to proceed!
Why would rabbit even Google Whacky words like deservance and aglet?
If the player carries out a Google search for a “Google Whack” (a search with only 1 result) using the words "deservance" “aglet" they will receive one hit.
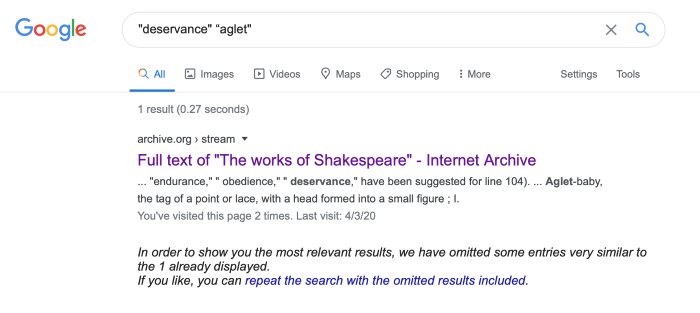
The hit URL is:
https://archive.org/stream/worksofshakespea03shak/worksofshakespea03shak_djvu.txt
The clue says the URL is all the player needs so from this they can extract the next flag.
FLAG
Worksofshakespea03shak_djvu
The HINTS for this challenge were:
I know Rabbit has always loved a good Googlewhack but they're harder to find these days! Rabbit "you" "cheat!”
Rash Decisions
We’ve had a recent sighting of Rabbit! He was last seen headed to a hidden webpage... bring home the bacon and continue the chase using the info in the text file!
222607922/10001001000001010000001001001010000000000000100001010001001000111011010101000100001010110101010010100110110100010110010000011011011010001100
This binary string can be converted to text using the Bacon Cipher Decode on CyberChef.
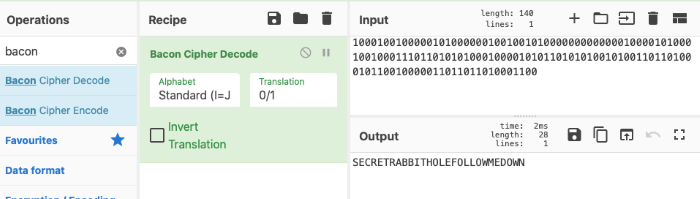
Adding this decoded binary back to our original string leaves:
22260792/secretrabbitholefollowmedown
Decimal IP can be decoded to a standard IP format using a website such as
https://www.ipaddressguide.com or can also be used without decoding directly in the web browser.
So the hidden page can be found at
Visiting this gives the next flag for the player to enter on the challenge CTFd site.
FLAGR4BBITISANESSENTIALW0RK3R
The HINTS for this challenge were:
So we're looking for a hidden webpage? Awesome, I just need to figure out the URL and I can follow Rabbit!
00111100101001001110://
(this binary is another Bacon Cipher string which can be decoded to http://)
Search Party
Rabbit is doing well at social distancing but where is he?
Dig deep to uncover the next flag and clue!
The player is provided with a download of a ZIP file named A.zip which has hundreds of images of seemingly matching images distributed across a tree structure of directories. The image is shown below.

Using a tool of their choice the player can compare the MD5 hash value of all the image files contained with the ZIP archive and identify the few images that are different to the rest.
There are extra bytes added at the end of each of these different image files which can be seen in a hex viewer. Sorting the images by file size will allow the player to extract the extra bytes in the right order to form a string. This string spells the following in hex format.
46-4c-41-47-52-34-38-38-49-54-53-54- 34-59 -41-54-48-30-4d-33
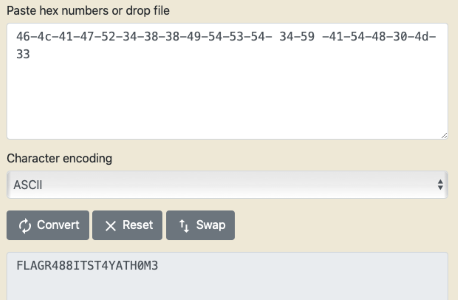
FLAG
FLAGR488ITIS4TH0M3
The HINT for this challenge was:
Wait a minute, not all these images are alike!
Final Snap Flag
You’ve nearly found Rabbit!
If you can find his final flag he’ll reveal himself and get back to work!
He says he already Tweeted the final flag but i don’t see any flags Tweeted at all. What now??
The player must find a Tweet that was deleted from the
@foxtonrabbit Twitter account but can still be found on a webpage archive website similar to WayBack Machine.
The player must find the following archive website to search for any archived tweets from the Twitter account.
This shows the tweet before it was deleted.
The final flag can be entered on the challenge CTFd website to finally catch the Rabbit!
FLAG
FLAGSELFISOLATIONVACATION!
The HINT for this challenge was:
Rabbit says it wasn't wayback when he tweeted the flag, but we should be able to find it somewhere!
Thanks again to all that played! Until the next time!