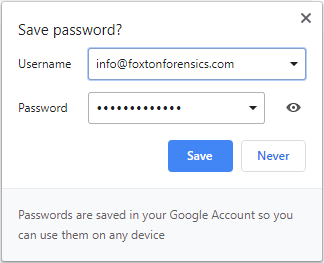
When a user logs into a website using Google Chrome the browser will offer to save the password.
Data related to saved passwords is stored within the Login Data SQLite database, which is typically in the following location on a Windows machine:
C:\Users\<username>\AppData\Local\Google\Chrome\User Data\Default\Login Data
If the user selects ‘Save’ on the dialog, a record is added to the logins table within the Login Data SQLite database.
Within the logins table usernames are stored in plain-text and passwords are encrypted. Other useful data is stored, such as the website URL, the timestamp the login was saved, and the number of times the saved login has been used.
If the user selects ‘Never’ on the dialog, a record is added to the logins table without the username and password details. This record has the blacklisted_by_user flag enabled to indicate that passwords shouldn’t be saved for this website. It is important to note that the times_used count is set to 0. Therefore, this count represents the number of times a saved login has been used not the number of times a particular website has been logged into.
If the user dismisses the dialog without selecting either option then a record is added to the stats table within the Login Data database.
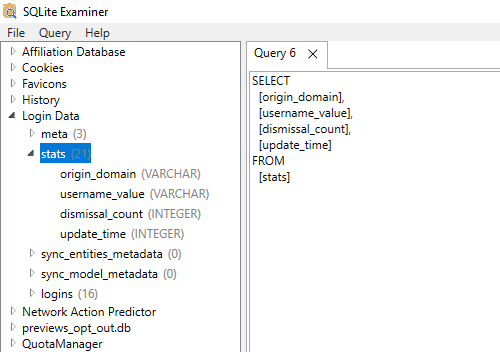
Within the stats table the following data is stored:
- Website domain
- Username
- Dismissal Count
- Update Time
Therefore, we can use this data to determine the usernames used to log into websites even when the user has not chosen to save the password. The dismissal count tells us how many times they have logged in using that username and dismissed the save password dialog. The update time tells us the last time they logged in using that username and dismissed the save password dialog. Records in the stats table are removed if the user subsequently chooses ‘Save’ or ‘Never’ on the save password dialog.
This information could prove very useful to an investigation, so it’s always worth checking the
stats table in addition to the
logins table within the
Login Data database. This can be done manually using a free SQLite viewer tool such as
SQLite Examiner.
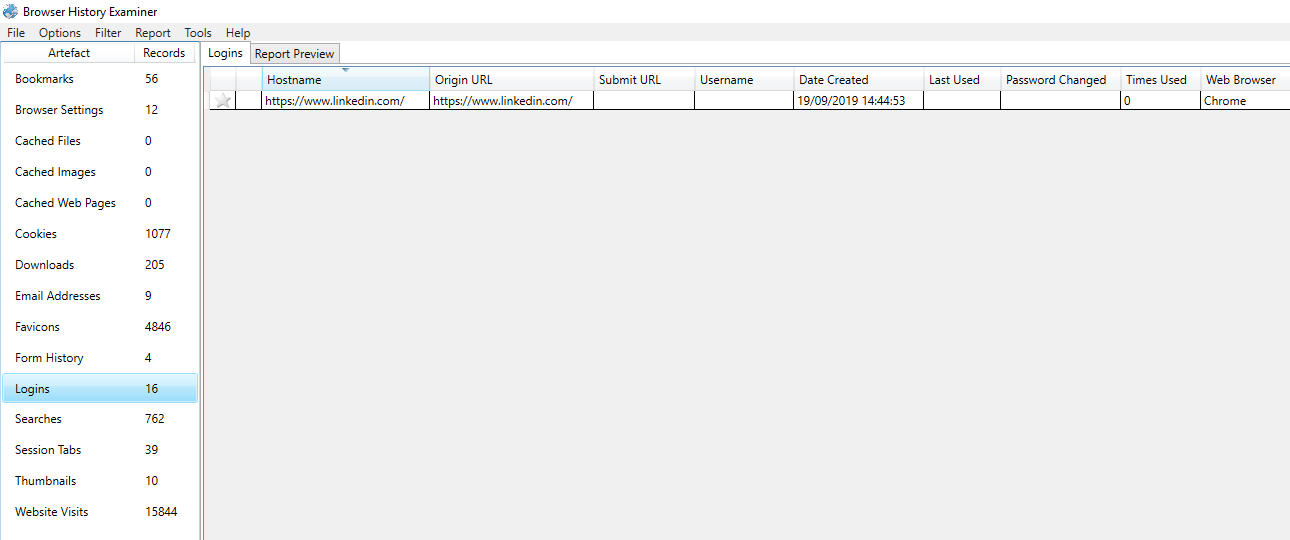
We have also updated
Browser History Examiner (BHE) to automatically extract this additional data source into the Logins dataset:
To try this out for yourself, visit our
Downloads page for a free trial of Browser History Examiner.