Whether you're a digital forensic analyst, a malicious cyber criminal or simply a security conscious computer user, we are all interested in how passwords are being transmitted, stored and secured on our computers and devices. We all trust that our web browser will be properly handling our passwords as we use them online. Unfortunately this is not always a choice made by our web browser. Poor security practises on the websites we visit can lead to our passwords being insecurely stored on our computer.
Previously, we discussed how it was possible to
link browser form history to web page URLs, and therefore determine the usernames and email addresses used to log into various online services, even when the user has chosen not to save the associated password. We have carried out further research in this area and revealed that under certain circumstances passwords can be inadvertently stored within the browser history in plain text.
This can occur on login forms that have a “show password” feature, that allows the user to view the password they have entered before submitting it. Depending on how this feature has been implemented by the website developer, if the user submits the form while the password is still visible then it may be stored in the browser’s autocomplete history in plain text. This assumes the browser has autocomplete enabled.
We reviewed the websites of a number of well known UK companies and found the following were susceptible to this issue:
All three rank inside the top 250 most visited websites in the UK according to
Alexa.
The following screenshot shows the login form for Ryanair.com, where the show password feature has been used.

If the user clicks ‘Log in’ with the form in this state then both the username and password will be stored in their browser history in plain text. This occurs even if they explicitly choose not to store these particular login details.
This is happening due to the way the show password feature is implemented. Passwords are usually entered into a HTML input element of type password. This ensures the password is masked and is not added to the browser’s autocomplete history.
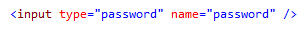
The 3 sites listed above all use the same technique to reveal the password to the user. The HTML input is changed from type password to type text, and therefore the password is no longer masked.
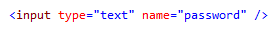
By default the value entered into input elements of type text will be stored by the autocomplete feature. Website developers can easily prevent this, therefore ensuring passwords are not stored locally in plain text, by adding the following attribute:
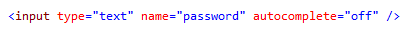
More details on disabling autocompletion of forms can be found at the following link:
https://developer.mozilla.org/en-US/docs/Web/Security/Securing_your_site/Turning_off_form_autocompletionFor forensic investigators these passwords could prove very valuable. Given that people often reuse passwords it may be that the same passwords, or variations of them, provide access to encrypted data or other online services associated with the user and may prove key to concluding an investigation. The screenshot below shows how the username and password are shown within
Browser History Examiner (BHE):
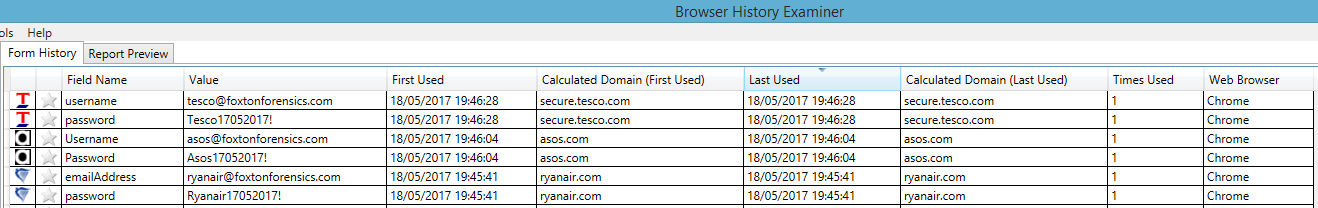
Whether you are a forensic investigator digging through internet history, a security professional or simply a home user, BHE can help analyse internet history for any plain text passwords that might be inadvertently stored there.
To try this out for yourself visit our
Downloads page for a free trial of Browser History Examiner.